Rackware RMM Migration
Getting Started for Oracle Marketplace (BYOL)
May 2021
Passthrough
Passthrough – RMM does not store a copy of the used data from source hosts. The RMM acts as a passthrough proxy to sync the source workload data through itself and onto the target DR instances.
RackWare Ocpu and memory requirements
Each Ocpu = 2 virtual cpu’s
Each host sync operation consumes one virtual CPU thread.
Example:
If you require to sync 8 hosts in parallel this would require 4 Ocpu’s
Minimum OCPU = 4
Minimum Memory = 16gb
1. Deploy RMM instance from the Marketplace listing.
a. Deploy RackWare RMM from Oracle Marketplace
b. For every 2 parallel sync operations the RMM instance will require 1 OCPU
i. minimum deployment of 4 OCPU and 16gb ram is required.
2. Configure RMM instance
a. Login through ssh to your RMM Instance
i. Connect with user opc and ssh key supplied when you deployed the instance.
b. Elevate opc user to root
i. All RMM operations are executed as root
ii. $sudo su -
c. Run the RMM configuration script and enter configuration options.
i. # rwadm init
ii. Modify iptables rules for RMM operations (Y/N) [Y]: Y
iii. Download ISO for linux vcenter autoprovision (Y/N) [N]: N
iv. Do you want to continue with enabling the hub-role for the RMM (Y/N) [N]: N
v. Changing password for user admin.
New Password:
enter a password that will be used for accessing the GUI through a browser as admin
vi. Do you want to add extra disk to RMM storage pool? (Y/N) [N]: N
vii. Configure: rmm: configure listening interfaces:
Available: ens3
Selected: ens3
viii. [A]dd, [R]emove interfaces for rmm to listen on, or [F]inished [F]: F
Do you want to configure NTP SERVER?
ix. This can be skipped in case of PS License type [N]: N
x. [A]dd, [R]emove NAT IP, or [F]inished [F]: F
Initialization Done.
3. License your RackWare server.
a. Generate your license pre-install file
i. #rwadm relicense
If you wish to continue using RMM till you get the new license, DO NOT STOP RMM after running this command.
ii. Do you wish to continue? (Y/N) [N]:Y
Preinstall file generated at /etc/rackware/rwlicense_preinstall_1234567890. Please email this file to [email protected] to get the license.
iii. DO NOT REBOOT
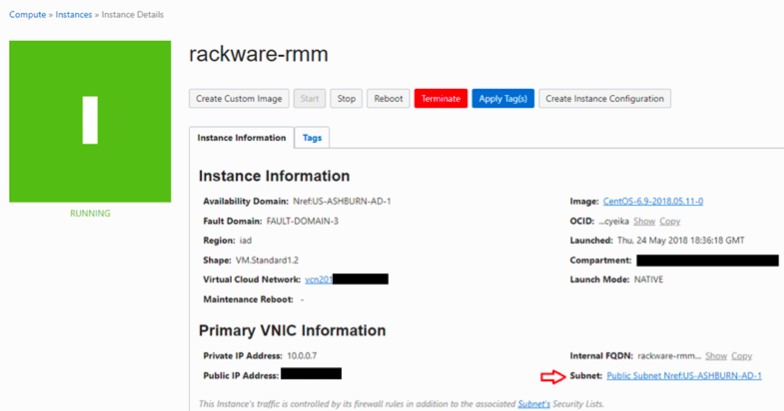
4. Configure your OCI Security list for access to RMM appliance.
a. Open TCP ports 22, 443 ingress to the RMM
b. Open TCP port 445 ingress from RMM to target subnet
c. From instance view click on the link to the subnet
d. Click the link to the security list for your subnet
e. Add a stateful Ingress rule from the IP or network where you will access the RMM
i. Click on Edit all rules
ii. Add the ingress rules to your RMM from the host you will access it from
5. Login to the RackWare RMM GUI
a. Open a Chrome or Firefox browser.
i. https://<rmm_ip>
ii. Username: admin
iii. Password: <this password you created from step 2c
6. Prepare your Linux source hosts
a. TCP port 22 should be open in any firewalls between source and RMM
b. Login to your Source linux host through SSH
c. Create user "rackware" on Source linux hosts
i. # sudo useradd -m -s /bin/bash rackware
d. Login to RMM and copy sudoers file information
i. rmm> #sudo cat /opt/rackware/docs/sudo-config.txt
e. Edit sudoer file on source host
i. source> #sudo visudo
ii. copy sudo-config.txt from RMM to bottom of sudoers file on source hosts
f. Create .ssh directory and authorized_key file for rackware user on source host
i. $ sudo su - rackware
ii. $ mkdir -p /home/rackware/ .ssh
iii. $ touch /home/rackware/.ssh/authorized_keys
iv. $ chmod 700 ~/.ssh/
v. $ chmod 600 ~/.ssh/authorized_keys
g. Copy RMM SSH key to source host
i. FROM RMM
ii. rmm> # sudo cat ~/.ssh/id_rsa.pub
h. Paste ssh key into source host authorized_keys file
i. $ vi /home/rackware/.ssh/authorized_keys
ii. $ sudo restorecon /home/rackware/ -v
i. Test connectivity between your RMM and your linux source host
i. rmm> #sudo ssh rackware@<my_source_ip>
ii. You should connect without any password prompt.
7. Prepare your windows source hosts.
a. TCP port 22 should be open in any firewalls between source and RMM
i. Open TCP 22 on the windows host. Enter netsh command in elevated powershell command (run as administrator).
1. netsh.exe advfirewall firewall add rule name=rw-tcp22-in dir=in action=allow protocol=TCP localport=22
2.
b. Download the RackWare SSH Client installer package to the source host.
i. https://<RMM_IP>/windows/RWSSHDService_x64.msi
ii.
c. Run the installer package with administrator level privileges
i.
ii. Accept the license agreement and click next
1.
iii. Accept default installation folder and click next
1.
iv. Copy and paste contents of your RMM’s public ssh key
1. RMM > # sudo cat ~/.ssh/id_rsa.pub
2. Copy the ssh key info
3. RMM > # sudo cat ~/.ssh/id_rsa.pub
4. Leave Username SYSTEM and Password fields blank.
5. Then click next
a.
b. Accept UAC
c.
d. Click Close
e.
d. Test connectivity between Rackware RMM and your windows source
i. From RMM
ii. # ssh SYSTEM@<windows_ip>
[root@rackware-rmm ~]# ssh [email protected]
The authenticity of host 'x.x.x.x (x.x.x.x)' can't be established.
RSA key fingerprint is 01:aa:02:bb:03:cc:04:dd:05:00:00:00:00:00:00:00.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added 'x.x.x.x' (RSA) to the list of known hosts.
[system@rw-win-source ~]
rackware$
8. Create your Wave file for Migration using passthrough (no source data stored on rmm)
a. Login to the RMM GUI using Firefox or Chrome browser
b. User: admin
c. Password: (password you set earlier)
d. Download the Wave template
e. Save the .csv to your local workstation for editing
f.
g. Edit the Wave file in Excel or an editor that can support tab delimited text file.
i. Add in the data for the following columns
1. Origin Name: Name of your source host – freeform no spaces
2. Origin IP: Can be ip address or FQDN that can be resolved on RMM
3. Target Name: Name you want your target host in OCI
4. Origin Username:
a. Windows = SYSTEM
b. Linx = Rackware
i. You created this user from step 5
5. Clonename: Name of your image to be stored in the rmm datastore
a. Leave blank unless you intend to keep a copy of your source host data on the rmm for Disaster Recovery purposes
6. OS:
a. windows
b. linux
7. Shape: Specify an OCI shape
a. Example: VM.Standard2.1
8. ssh only
a. for windows = TRUE
b. for linux leave blank
9. operation: host sync
Example:
9. Upload Wave file to RMM
a. Login to the RMM GUI using Firefox or Chrome browser
i. User: admin
ii. Password: (password you set earlier after licensing RMM)
b. Click on the upload file icon and browse the local file system for your edited wave template.
c.
d.
e. The wave list will load and the detailed list of individual servers to be migrated will appear.
f.
10. Gather your Oracle OCI account information.
a. Api url for your region, Examples:
i. https://iaas.us-ashburn-1.oraclecloud.com
ii. https://iaas.us-phoenix-1.oraclecloud.com
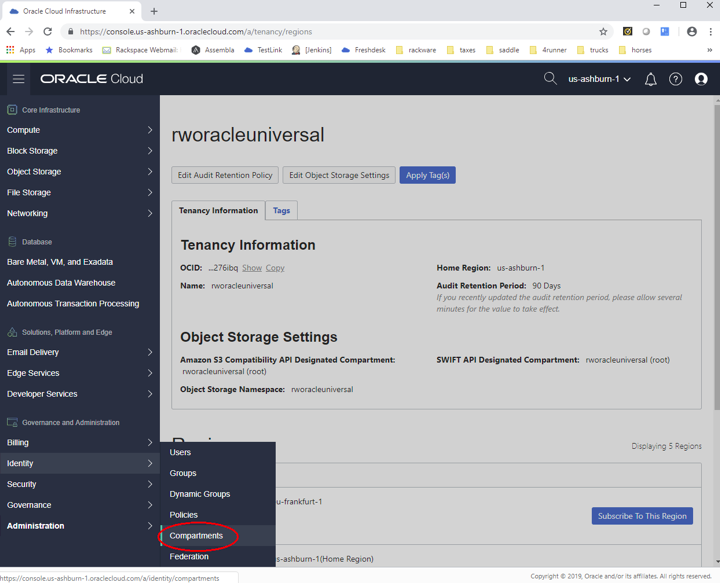
b. User ID
i. From your OCI console. Select Identity > Users
ii.
iii. Copy the OCID for your user and paste it to a text file for now
c. Private Key File Path
i. Generate an API signing keys
1. Login to your RMM and elevate yourself to root level as described in license instructions earlier
2. #mkdir ~/.oci
3. # cd ~/.oci
4. # openssl genrsa -out ~/.oci/oci_api_key.pem 2048
5. # chmod go-rwx ~/.oci/oci_api_key.pem
6. # openssl rsa -pubout -in ~/.oci/oci_api_key.pem -out ~/.oci/oci_api_key_public.pem
7. Show the key values and copy to clipboard
8. cat ~/.oci/oci_api_key_public.pem
9. reference: https://docs.cloud.oracle.com/iaas/Content/API/Concepts/apisigningkey.htm
10. get path to your key and copy it to notepad
a. # cd ~/.oci
b. # pwd
/root/.oci
c. Your private key path is: /root/.oci/oci_api_key.pem
d. Generate your OCI fingerprint
i. From your OCI console click on your user account as show above
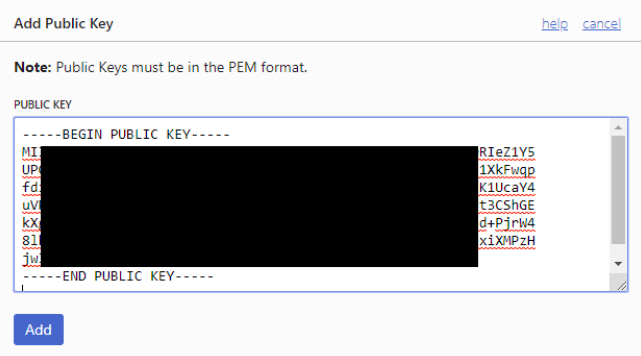
ii. Select the link “Add Public Key”
iii.
iv. Copy the contents of the pubic key that was generated in the previous steps into the Add Public key window
v.
vi. Copy your fingerprint to notepad for input later
vii.
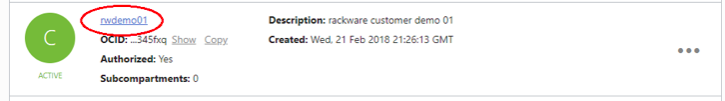
e. Tenant ID
i. Gather the tenancy id and save for input later
ii.
iii. Passphrase: if you created an rsa key with passphrase (not mandatory)
iv. Compartment Name – if other than the root compartment
v.
vi.
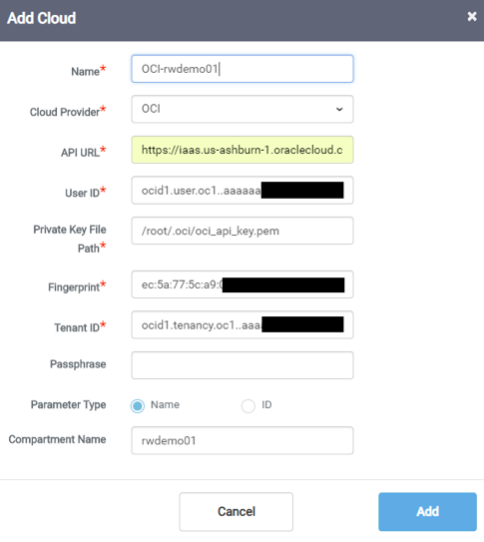
11. Add your OCI account information to the RMM Cloud Configuration
a. Login to your RackWare RMM Console
b. Expand the “Configuration” Tab on the left, select “Cloud” and click on the Add button
c.
d. Change Cloud Provider to OCI
i.
ii. Input the information into all the additional fields from the previous section
iii. Name can be any name you wish to give this configuration
iv.
v. Click Add
vi.
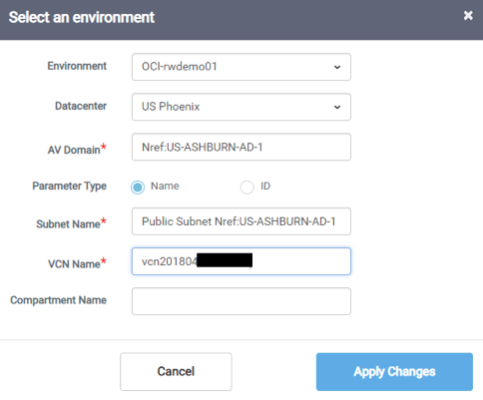
12. Attach your OCI account configuration to your Wave
a. Expand the Replication Option, click on waves and click on the blue link to your wave
b.
c. Click on the blue “Not configured” link
d.
e. Select your environment – the cloud user you set up in the previous step.
f. Enter the additional parameters
i. Datacenter
ii. AV Domain example (Availability Domain):
1. Nref:US-ASHBURN-AD-1
iii. Subnet Name
iv. VCN Name
g.
h. Click Apply Changes
i.
13. Start your Migrations
a. Set the parallel count to the number of migrations to run concurrently.
b. Press the play button
c.
d. Status will change to running and the hosts will start their migration from source datacenter into the specified OCI environment.
e.
f. Login to your OCI console to watch the new hosts being deployed.