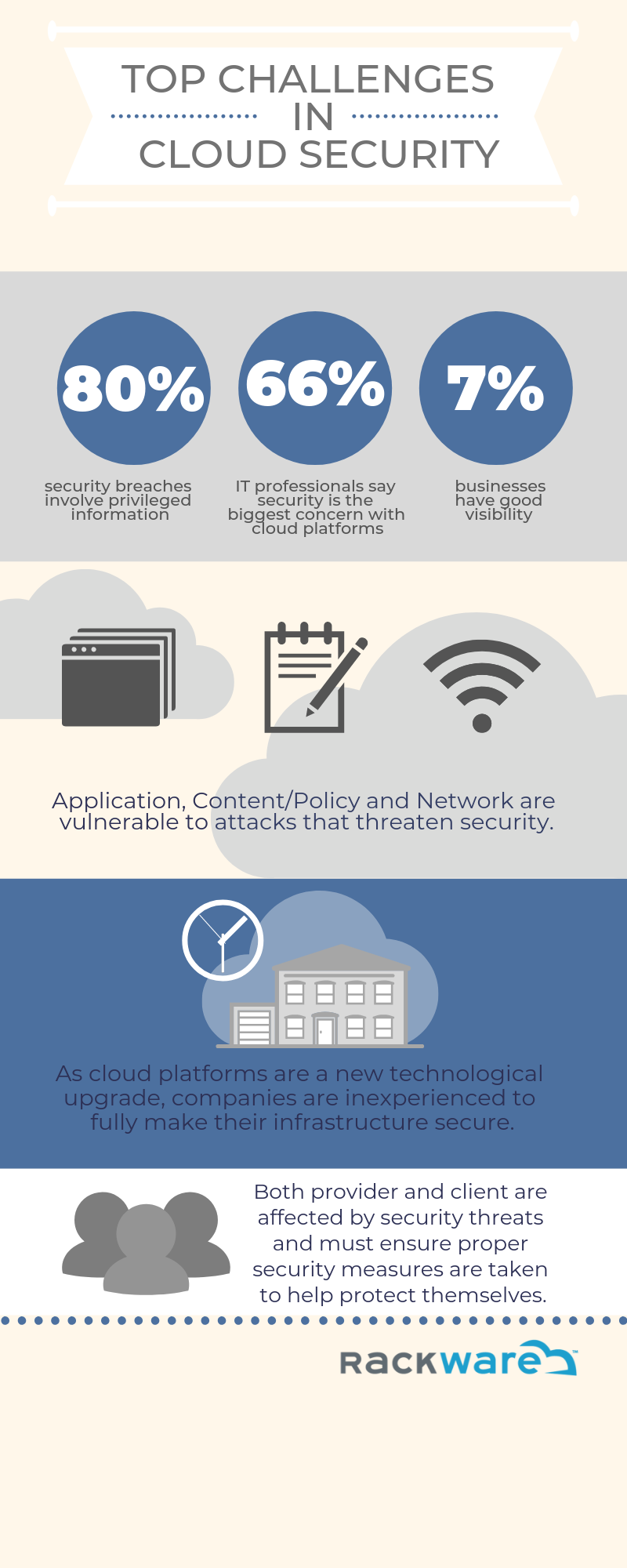
Top Challenges in Cloud Security
Cloud computing is an internet based computing where all resources are shared with software and information available and accessible on demand anywhere anytime. An array of benefits for an IT team can result from transitioning to cloud computing. Being a fairly new technological adaptation to enterprises, there are bound to be concerns.
Security Issues
As information applications move further from IT organization, visibility and control is lost. Most cloud providers are performance and scale centric, so governance data and application security can be easily overlooked. All cloud based security issues can be broken down into four departments. Risks include data integrity, application security, content and policy security, and network level attacks.
Here are possible occurrences that threaten data integrity:
Data breaches, locks, and removals are among the possibilities that can risk in the loss of data integrity. Data breaches are incidents in which sensitive data are stolen by individuals who have no authorization to do so. Also referred to vendor lock-in, data lock is a situation in which customers using a service cannot easily convert to a competitor’s product or service, usually as a result or incompatible technologies. In the case of data removal where there is a rendering representation of data loss, recovery may become difficult if the server broke down or failed.
Application Security Issues
Share this Image On Your Site
Emerging attacks called denial of service (DoS) and distributed denial of service attacks (DDoS) are among the top ways that risk application security. DoS and DDos attacks are when legitimate users are prevented from accessing the service commonly through flooding. Flooding targets machines or resources with excessive requests to overload systems that prevent legitimate request from being met. Other possible application security issues can result from cloud malware injection. The attacker, in this case, focuses on inserting harmful implementations to cloud services. In other instances, cookie poisoning can modify a user’s cookies so the attacker can gain unauthorized information for identity fraud. Backdoor attacks is a conventional technique that bypasses system security undetectably to directly access user information directly in the cloud. Through hidden filters on webpages, hidden field attack attackers yield and collect unauthorized information.
Content / Policy Level Security Issues
When attackers identify two virtual machines hosted on same physical hardware and attempt to penetrate one machine from another, it is called guest hopping. Another way of attack is through SQL injection in which the attack embeds a malicious code into a poorly designed application and then passes it to the back-end database. An inside channel attack refers to a cache attack when cache accesses are monitored to gain encrypted data. At times, a person or employee will attempt to threaten enterprises since they have access to their system and data.
Network Level Attacks
Lastly, network level attacks are among the security risks of cloud computing. A DNS attack includes domain hijacking and cross site scripting that can be costly for enterprises. When intruders sends malicious data to computers with an IP address that indicates the message originates from a trusted host, this is known as IP spoofing. A man-in-the-middle attack, communication between two users is monitored by attackers to gain confidential information. To conclude network level attacks, sniffing is an attack in which data is captured and interpreted while flowing through the network. The attacker is able to gain access to all information that is transported through the network.
Security issues are faced by cloud providers as well as also faced by their customers.
Providers must make certain that their infrastructure is secure and that their clients data and applications are safe-guarded while ensuring that the proper security measures are taken to protect their information.